Post-Quantum Security | 매거진에 참여하세요
Post-Quantum Security
#Quantum #PQC #Lattice #Security #DigitalTru
Rethinking Encryption in the Age of Quantum Computing: The Warning from Quantum Computers
Our financial transactions, corporate secrets, medical records, and even casual messages all rely on encryption.
It’s the invisible shield of the digital era.
But that shield may soon shatter.
The reason? Quantum computers.
Unlike today’s supercomputers, quantum machines have the potential to solve in minutes what would take billions of years with classical hardware.
Most alarmingly, they could break RSA and ECC , the encryption algorithms that secure nearly all of today’s internet.
Governments, corporations, and researchers worldwide are now racing to prepare for a new era of cryptography
: Post-Quantum Cryptography (PQC).
The Quantum Threat to Encryption
Modern cryptography assumes certain math problems are “too hard” to solve quickly.
For example, RSA is secure because factoring large numbers is infeasible with classical computing.
Quantum computers change that. With Shor’s Algorithm, they could factor numbers and thus break RSA with shocking efficiency:
RSA 2048-bit
- Classical supercomputer: billions of years
- Quantum computer (large enough): hours, or less
The implication is clear: once a sufficiently powerful quantum computer is built, the entire foundation of today’s digital security could collapse overnight.
Enter Post-Quantum Cryptography (PQC)
To counter this, researchers are building new algorithms that resist quantum attacks. PQC has three key traits:
New Mathematical Foundations
Instead of factoring or discrete logs, PQC relies on problems like lattice structures or hash-based schemes.Quantum Resistance
Even with quantum computing, these problems remain computationally hard.Standardization
The U.S. National Institute of Standards and Technology (NIST) has been running a global PQC competition since 2016, and in 2024 selected its first official algorithms (e.g., Kyber, Dilithium).
Tech giants are already experimenting: Google has tested PQC in Chrome, while IBM and Microsoft are preparing PQC integration in their cloud services.
Why Lattices Matter
Lattice-based cryptography is at the heart of PQC. Imagine an infinite grid of points in high-dimensional space — finding certain points or relationships within that grid becomes incredibly difficult.
Some of the key problems include:
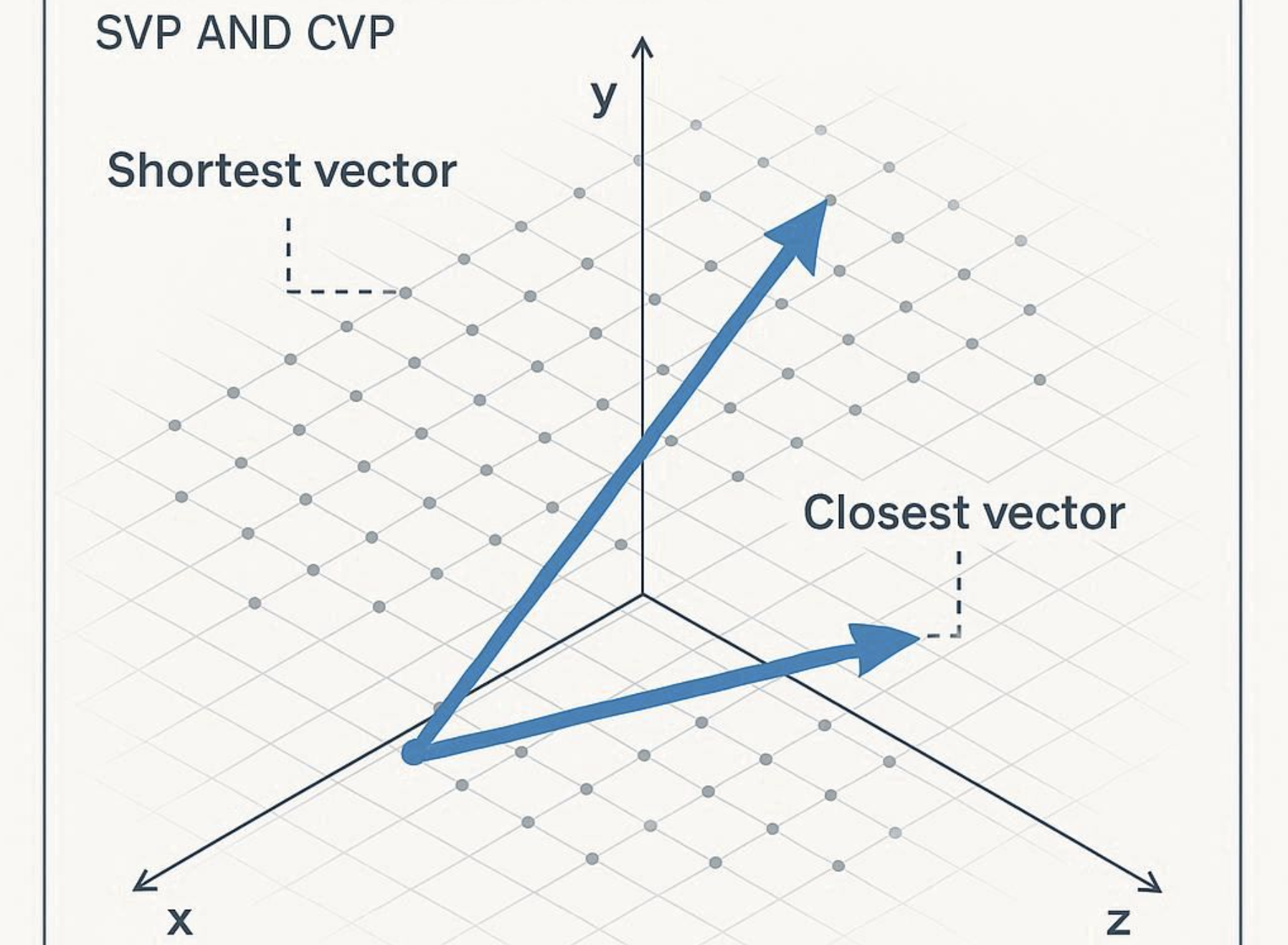
SVP (Shortest Vector Problem)
Find the shortest nonzero vector in a lattice. Sounds simple, but it’s computationally brutal.CVP (Closest Vector Problem)
Given an arbitrary point, find the nearest lattice point. Easy in 2D, but impossibly hard in hundreds of dimensions.LWE (Learning With Errors)
Solve noisy linear equations. The “errors” make it resistant even to quantum attacks.Ring-LWE / Module-LWE
More efficient versions, forming the backbone of real-world PQC algorithms.
These problems aren’t just abstract math puzzles — they are the building blocks of the next era of digital security.
Business Implications: Beyond the Lab
Quantum-resistant encryption is not just a technical issue , it’s a business survival challenge.
Finance
Banks, exchanges, and blockchain platforms must prepare for “quantum-safe wallets.”Healthcare
Patient records are too sensitive to risk. PQC adoption will be mandatory.Government
National security depends on transitioning before adversaries weaponize quantum computing.Startups
Security, fintech, and cloud startups can seize the “quantum-ready” market opportunity.
On forums like Reddit, security professionals warn: “Companies that don’t prepare for post-quantum encryption won’t survive the next decade.”
Between Hype and Reality
Let’s be clear: today’s quantum computers still lack the thousands of stable qubits needed to break RSA.
So no, the internet won’t collapse tomorrow.
But migration matters.
According to NIST, replacing existing cryptographic infrastructure could take 10+ years , especially in finance and government, where legacy systems run deep.
That means the time to prepare isn’t when the threat arrives , it’s now.
Conclusion: Only the Prepared Will Survive
Post-quantum cryptography isn’t just a research project for academics.
It’s a question of digital trust , the foundation of every business and every online interaction.
The next 5–10 years will determine which organizations maintain that trust and which lose it.
In 2025, we don’t need to panic about quantum computers yet.
But complacency is dangerous.
The post-quantum era is coming, and in that world, security is no longer optional — it’s the price of survival.






